Conduit mLinux: Advanced LoRa Configuration
Additional LoRa configuration fields in /var/config/lora/lora-network-server.conf:
| Item | Description | |
| db | Non-volatile location of the LoRa network server database file. | |
| backupInterval | Interval in seconds to backup database to non-volatile memory. | |
| lora | LoRa network configuration: | |
| Item | Description | |
| frequencyBand | 868 or 915. | |
| channelPlan | Set of frequencies and datarates to use for uplink and downlink channels. EU868, US915, AU915, AS923, IN865, RU864 or KR920. | |
| frequencySubBand | Sub-band for US operation, 1-8. | |
| rx1DatarateOffset | Datarate offset for mote RX window 1 sent in join response (0-3). | |
| rx2Datarate | Datarate for mote RX window 2 sent in join response (7-12). | |
| maxTxPower | Max TX power (dBm), -6 to 26. | |
| antennaGain | Gain of external antenna in dBi, default: 3 | |
| deviceQueueSize | Max number of downstream messages in queue per each device. | |
| frequencyEU | Center frequency for extra EU channels (Hz). (865.5-867.5 or 869.4 MHz) | |
| frequencyAS | Center frequency for extra AS channels (Hz). (920.5-922.6 or 924.1-927.5 MHz) | |
| frequencyKR | Center frequency for extra KR channels (Hz). (921.3-921.5 or 922.9 MHz) | |
| netID | Net ID for beacon packets and assigned network addresses. | |
| beaconInterval | 0:disabled, N:seconds between beacon packets, must be factor of seconds in a day. | |
| beaconPower | dBm to transmit beacon packets. | |
| beaconFreqHop | Enable/disable frequency hopping for beacons in AU or US. | |
| beaconFrequency | Frequency for beacon packets, set to 0 for default according to Channel Plan. | |
| beaconInfoDesc | gw desc indicator. | |
| beaconLatitude | Latitude value to add to beacon packets gw desc field. | |
| beaconLongitude | Longitude value to add to beacon packets gw desc field. | |
| ADRStep | Step in cB between SNR based datarate assignment for ADR | |
| dutyCyclePeriod | Length of duty-cycle sliding window in minutes. (default: 60) | |
| minDatarate | Min datarate for ADR, default: US915/AU915 DR0 – SF10BW125, EU868 DR0 – SF12BW125 | |
| maxDatarate | Max datarate for ADR, default: US915/AU915 DR4 – SF8BW500, EU868 DR6 – SF7BW250 | |
| joinDelay | Rx1 delay in seconds between end of tx and opening of first rx window for join accept message | |
| rx1Delay | Rx1 delay in seconds between end of tx and opening of first rx window | |
| syncWord | Sync word override to configure Sx1301 concentrator in decimal notation, (public: 52 (0x34), private: 18 (0x12)) | |
| maxEIRP | AS923 max device TX power, default: 20 | |
| dwelltimeUp | max dwelltime for uplink packets, default: 0 – no limit, 1 – 400 ms | |
| dwelltimeDown | max dwelltime for downlink packets default: 0 – no limit, 1 – 400 ms | |
| enableStrictCounterValidation | ensure packet counter values are not being reused, packets are dropped if not within MAC_FCNT_GAP, default:true | |
| schedulePaddingMs | time on air padding for scheduling downlink packets in ms | |
| lbtEnabled | Enabled listen before talk, if additional channels are set only 7 channels will be used to allow Rx2 downlink, default:false | |
| lbtThreshold | RSSI threshold reading must be below for transmit, default:-65 | |
| lbtScanTime | Listen before talk scan time, default: 5000, (128 or 5000 us) | |
| lbtSxOffset | Offset applied to Sx127x RSSI reading used in LBT and Spectral Scan, default: -24 | |
| sxOffset | Offset applied to Sx125x RSSI reading, default: -162 | |
| udp | UDP clients/servers configuration: | |
| Item | Description | |
| allowPublic | Allow binding to the public interfaces. | |
| upstreamPort | Port for udp clients to listen to upstream packets, such as packet-forwarder. | |
| downstreamPort | Port for udp clients to listen to downstream packets, such as packet-forwarder. | |
| appPortUp | Port to receive upstream packets from application. | |
| appPortDown | Port to send downstream packets to application. Port expected on 127.0.0.1 | |
| addressRange | Range of addresses to assign from: | |
| Item | Description | |
| start | Range start. | |
| end | Range end. | |
| network | Network settings: | |
| Item | Description | |
| public | Enable public compatibility mode: changes the join response time from 1 to 5 seconds and the sync word from 0×12 to 0×34 | |
| leasetime | Expiration of network addresses after inactivity in minutes. | |
| name | Network name, used to generate EUI. | |
| passphrase | Network passphrase, used to generate key. | |
| defaultProfile | Default profile used for device joined using Name/Passphrase or NetworkID/NetworkKey. | |
| eui | Network ID, EUI. (64-bit HEX) | |
| key | Network key to use for encryption. (128-bit HEX) | |
| baseKey | Key used for zero touch provisioning (128-bit HEX) | |
| salt | Salt used for zero touch provisioning, random characters of any length | |
| whitelist | List of end device credentials permitted to join the device (gateway): | |
| Item | Description | |
| enabled | Enable OTA join of devices in whitelist. | |
| devices | Array of end-devices and keys with the following format: { “deveui”: “0011223344556677”, “appeui”: “7766554433221100”, “class”: “A”, “appkey”: “00112233445566770011223344556677” } |
|
| deveui | Hex EUI of end-device. i.e. 0011223344556677 | |
| appeui | Hex EUI of end-device. i.e. 0011223344556677 | |
| appkey | Hex Key of end-device. i.e. 00112233445566770011223344556677 | |
| class | A, B or C | trafficManager | Filters for join requests to be forwarded to remote join server |
| Item | Description | |
| enabled | Enable/disable traffic manager | |
| joinEuiFilter | List of EUI values or Min/Max ranges of EUI values. i.e. [ [ “00-00-00-00-00-00-00-01”, “00-00-00-00-00-00-00-04” ], “00-00-00-00-00-00-00-05” ] |
|
| devEuiFilter | List of EUI values or Min/Max ranges of EUI values. i.e. [ [ “00-00-00-00-00-00-00-01”, “00-00-00-00-00-00-00-04” ], “00-00-00-00-00-00-00-05” ] |
|
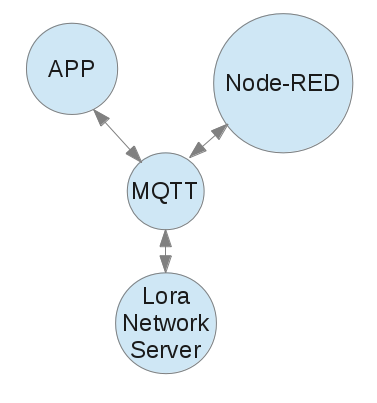
| mqtt | Messaging protocol used for intra-process communication: | |
| Item | Description | |
| enabled | Connect network server via mqtt. | |
| host | Broker host. | |
| port | Broker port. | |
| log | Log settings: | |
| Item | Description | |
| console | Output to stdout. | |
| syslog | Output to syslog. | |
| level | Level of messages, 0-100 (10:error, 20:warning, 30:info, 50:debug, 60:trace). | |
| path | Path to log file. | |
| test | Test settings: | |
| Item | Description | |
| disableRxJoin1 | Disable sending join accept on Rx1 Window. | |
| disableRxJoin2 | Disable sending join accept on Rx2 Window. | |
| disableRxWindow1 | Disable sending downlink packets on Rx1 Window. | |
| disableRxWindow2 | Disable sending downlink packets on Rx2 Window. | |
| disableDutyCycle | Disable duty-cycle restrictions for testing (DO NOT USE FOR DEPLOYMENT!) |
|